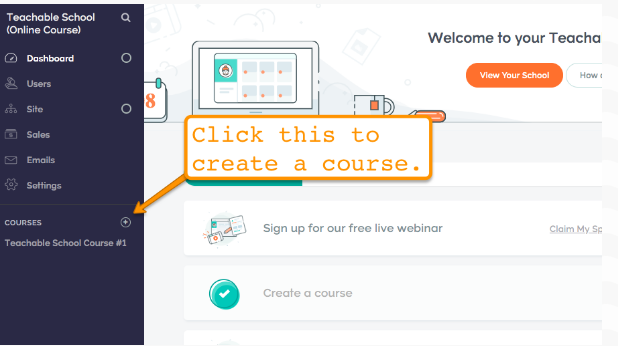
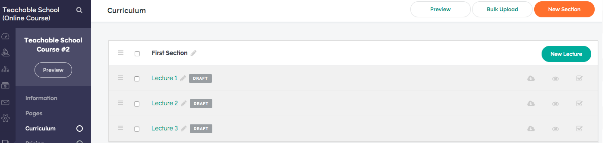
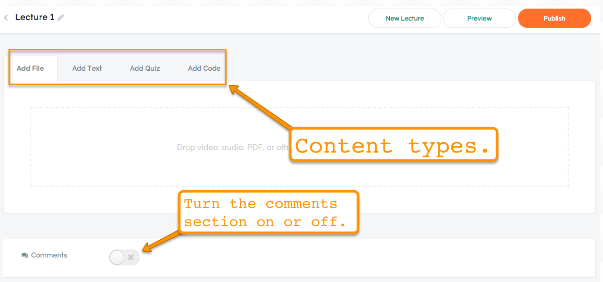
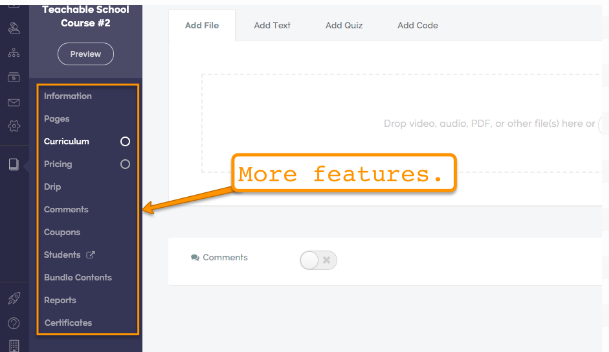
My Blogger Tricks |  |
- Power Grids Facing Risks Of Cyber Attacks
- Safe File Sharing : Everything That You Want To Know
- How safe are the Cryptocurrency transactions?
| Power Grids Facing Risks Of Cyber Attacks Posted: 11 Jul 2019 04:09 AM PDT  Citizens, who are part of the countries with eruptive dominion, stand a chance to be the worst victims of this phenomenon. The probability of civil unrest due to the political upheavals that have been making headlines recently is not distant in a country like Venezuela. The most shocking incident that took place in Venezuela was when the entire nation and its people went through a blackout for almost a week long's time that occurred as a result of the episode that took place on its adjacent land. Among the numerous reasons attached to this suffering, what has turned out to be pivotal is the overburdening and failure of the principal power lines that have produced several cyber-attacks as its consequence. Learning this fact, we cannot help but voice out a few questions that are raised in our minds. In the following section, we will strive to analyze and reason out the causes of these colossal losses. Reasons behind attacking power gridsOne thing that in today's world is growing with ferocious velocity is technology and its bearers, whose reverberation is a powerful intercommunication between the electronics that rule our daily lives. What seemed to be a mere dream 10 years ago, has not only established itself as the actuality but is constantly influencing our daily chores.It is no brainer that the world today without internet can be leveled to a man devoid his car; the world that has so far been running will begin to crawl at the speed of a turtle. Over the years we have converted the luxury of the internet to a necessity and cramped the entire macrocosm on our mobile screens. We have become so dependent on this service that today, the power-generating plants and utility companies depend on cyberspace for their functioning. Firms operating and managing through the internet, therefore, should remain extra cautious when it comes to their security, so that the confidential information that is indispensable in the making or breaking of the company, should be saved from its vulnerability to threat-imposing information mongers. Demolishing one's empire by directly attacking on land, sea or in the air is now a thing of the past. The trend that has seeped into our civilization is cyber warfare, whose primary weapon is wide-scale power outrage. Assailants have taken this course because of its capability of taking down a considerable scale of masses in a single shot. The areas that can be affected the most by these attacks are transportation and water supply and treatments. Once these basic needs of man are terminated, the ends of the attackers are successfully met. Popular ways of launching cyber attacksUnlike the other fields targeted for cyber-attacks, the ones which are directed towards the power-grids do not require investing great skilled hacking or web operation; a systematic and disciplined step-by-step approach is enough to break into their systems.If we look back into the history of such cyber-attacks, one accident that remains glaring is how the whole city lost all its power for an hour as a repercussion of a systematic attack on Ukraine's power grid. When the matter was further investigated, the malware named as "Industroyer", was behind the massacre. The aim was reached by capitalizing on the vulnerability known as CVE-2015-537. A similar attack that grabbed the spotlight was at Saudi Arabia that led to the blocking of a paramount oil company back in 2012. Everything took place around an e-mail that was opened by a secretary of the company without detecting whether it was already infected with the virus. In a matter of seconds, the virus infected the computer, cloning all its information in favor of the attackers. A stark difference between these two incidents is that the former occurred as a result of mechanical steps taking advantage of hardware jeopardy, while the latter was nothing more than common human error. Raising cybersecurity awarenessEven after several attempts of protecting ourselves from cyber threats, important information is lost in the web-space daily. The few measures that can curb this to some extent are using antivirus applications, unusual and distinct passwords and prevention of web tracking. Above all, the entity using the web service should be well aware of the security initiative and its usage to ensure an error-free functioning within their networks.New systems have been introduced recently that not only depend on educating its user but once turned on, protects all the data sent and received. The VPN application is the most common that is easily available even in the tiniest space of our homes. Apart from these external measures, when it comes to online security, the individual's or company's awareness regarding its usage stands peerless. What lies in the near future?In the recent past, we have shifted our reliance considerably to renewable power sources such as solar panels, fossil fuels, batteries, coal that helps to store a greater mass of power. These methods are not only restricted to massive energy plants but have also made their way into private homes. But the cyber threats attached to these methods are critical. With an increased number of individuals taking part in power production along with power plants have led to the swelling of the responsibility of wisely maintaining the digital networks that are connected and dependent upon one another. Coming to security, this will automatically run into the creation of more cyber security firms.In the present day, the USA stands as the leader of cyber security providers with over 850 cyber-security firms already established in the greater part of Washington DC. There are different studies that provide different pictures of this production. It predicts that mass users of the corporate network will soon shift to individual users, along with the forthcoming of a global shortage of 1.8 million cyber security professionals by the year 2022. ConclusionWe cannot deny the statement that today, all of us re equally part of the globalized village that we have created for ourselves. With every single aspect of life being internet-borne, our surrounding environment and inevitable needs will be sincerely attended by digitalization.Coming to the bottom line of cyber security, it is the fact that an individual's role in data protection is primary and therefore cannot be overlooked. However much the government and private firms try to introduce and establish cyber-security methods, it boils down to the individual's awareness and education regarding its wise application. One, while browsing through the internet, should ensure that every detailed looked up and traced should not reach anyone else none of the suspicious data sources should be opened or granted permission without a proper understanding of its role and functions. |
| Safe File Sharing : Everything That You Want To Know Posted: 11 Jul 2019 03:57 AM PDT  While sharing data between various places and people, one needs to be careful about various risk factors involved. It is advised to follow adequate safety measures to ensure complete safety for both parties exchanging data digitally. Although it is quite difficult to secure files during transfers, the best idea is to stay informed and equipped to address the associated threats on time. The very first step that we need to take for keeping files secure during transfers is to understand the basic concept of file sharing. Basics of file sharingIn simple terms, file sharing can be defined as transferring or sharing of files on a private or public network. As per the accessibility permissions, people connected via the network are allowed to edit and view files to meet their specific needs. There are endless practical applications of file sharing, It can be used for workplace-based communications, as well as for the worldwide multimedia networks that can be further accessed by millions of users.Several methods of data sharing have been already invented, and each one of them has unique pros and cons. In order to ensure the secure transfer of data over networks, it is first important to understand various methods available to execute this task. Below we have highlighted some of the most trusted ways to transfer data between two users:
Hope you have gone through all the popular file-sharing techniques and collected basic idea about how they work. It is time to go through the risks associated with these transfers and talk about the possible preventive measures. Risks associated with filing sharing:There are many file sharing activities when users need to pay more attention to safety; especially while sharing important documents at the workplace. Now, the biggest question is that from what we have to protect them? There are a number of risks that may affect file sharing activities; few of them are listed below:
Above we have listed the major risks associated with filing sharing services. The moment you understand the impact of these risks on usage and design of file transfer activities, it becomes easier to find ways to protect them. Although, some of these file sharing risks can be easily avoided with proper education and training; however, others are not that easy to handle. For example, if you are interested in ensuring protection against malware, it is not enough to be careful about your downloads. Sometimes, the infected files can affect network security, and it causes huge trouble to the businesses and individuals as well. In such cases, it is more important to find a suitable hardware or software solution to ensure proper protection for file transfer activities. There are so many methods to follow secure file transfer modes, and once you understand those techniques, it can keep your data safe for the long run. Some of the most trusted solutions are using specific p2p services, working via secure protocols, and using well-protected cloud servers. Secure File Sharing via Protocols or VPN:You can find numbers of encrypted protocols that ensure safe transmission of sensitive data between various users connected on a network. Some of the most trusted ones are SFTP and SSH. Other than this, you can establish a secure connection via VPN based encryption.Virtual Protocol Network (VPN) makes use of secure protocols and powerful encryption techniques to establish a connection via specific servers that can be located in different countries. With this, you can ensure high-end safety for your sensitive data, and at the same time, users can hide details about where they are connected while performing the online activity. Using a VPN is one of the most trustworthy ways to ensure safety and security. Secure P2P services:It is also possible to execute secure file transfers via peer to peer networks as well. One of the best examples of secure P2P services is Resilio. Although such networks provide a secure experience for file sharing, it is advised to follow safe downloading practices while working on a P2P network.About the author: John Dee is a Mac addict with a strong background in analyzing and combating security threats to the Macintosh ecosystem. John runs MacSecurity.net website specializing in malware research, software reviews, and groundbreaking industry news. It is his firm belief that underestimating Mac malware is like ignoring the elephant in the room. In his day-to-day work, John focuses on identifying new electronic perils potent enough to create ripples on the Mac security arena. On top of that, he is particularly enthusiastic about implementing effective countermeasures to fend off these menaces. |
| How safe are the Cryptocurrency transactions? Posted: 11 Jul 2019 03:43 AM PDT  The utility of cryptocurrency payments
Such speed and ease have made cryptocurrency payments the most favorable method for most upcoming startups as it checks the cost works smoothly. Cryptocurrency payments in actionThe process of payment will start off after registering at a cryptocurrency exchange. Following the registration, a wallet is created from where the coins are sent or are deposited in. One can also store the coins offline by using a computer-based wallet.The wallet will provide its user with two keys; a private key and a public key. The private key will enable the access to the wallet and performs in a manner similar to log in or password security; while the public key allows others to send the individual coins, and is subject to changes after each transaction. Therefore if one wants someone to send them coins, they are only liable to share their public key, taking help of which the sender can easily dispatch the cryptocurrency payment to the receiver's wallet. Likewise, if you want to send coins to someone else, all you will need is the public key of the receiver. The public cryptocurrency codes are shared by many business codes like QR codes. Once the QR code is scanned by the device, the account is precisely acknowledged by the software that will direct a payment request or the payment itself. Therefore, the time required for the procedure is incredibly little making it hassle-free. Cryptocurrency payments security concernsKeeping aside the convenience of cryptocurrency payments, the process can pose a threat to security concerns. The registration is conducted for the online exchange of coins in the wallet. Procuring coins requires one to provide his bank or credit card details. Even though this information is secured secretly, it might seem transparent on a hacker's part to lay open all the inputs. Such incidents have taken place before and aren't uncommon in the world of cryptocurrency.Also, the latest technologies have made it possible to trace the transactions through the P2P network, although the essential part of this is balancing enough number of nodes. This is thereby reason enough to secure all the information through VPN while conducting an important transaction. Another drawback here is that there is no scope for a refund once the transaction has been successfully completed. Ways to improve cryptocurrency payment securityOffline storage of Private KeyThe private key provided to you after the creation of the cryptocurrency wallet will grant your access to it. It has been duly observed that during many times, the private key of the user is stored online or within the network that hosts the wallet. Such scenarios can lead to the loss of information if a hacker attacks the network and access to the private key means direct access to the wallet.The best way to prevent this mishap is to enable offline storage for the private key, and in this case, the recommended is a choice of storing it in a device that does not have internet access. Keeping the key away from the internet will automatically separate it from the hands of the intruder. Creation and offline storage of a private key needs some effort. The cryptocurrency transaction will need you to connect a USB to the computer devoid of internet service and verified every single time it is performed. This might be a little time-taking but is the most reliable when it comes to the cryptocurrency transactions. Cold and Hot WalletsA hot wallet in a cryptocurrency transaction is the one which is either online or connected to an exchange. Because of its online status, it is more welcoming to the attacks of the hackers. Compared to a hot wallet, a cold wallet exist offline and is capable of providing better security to the former type.The best way to ensure the Cryptocurrency transaction is to use a combination of the hot and cold wallets. The idea is to store the excess available coins in the cold wallet so that they can be kept away from hacking threats and keeping a limited number of coins in the hot wallet which is to be used for a regular use, so that if in any case the hot wallet is preyed upon, the user will not face grave loss. VPNsVPNs have been widely used by all sectors of the society; the government, multinational companies and at the same time individuals to keep safe their cyber information. Apart from rerouting the traffic, the VPNs, at the same time, encrypts the data traveling between the two nodes of the user's device and the opposite end, which can be a website or server. Top-rated VPN applications are being used by activists, journalists, hackers and other groups of privacy-sensitive mass.Along with the other two methods, VPN is equally effective when it comes to cryptocurrency transaction security. The traffic of the communication is justly kept track of and the data that is being used during the sending and receiving of payments. There is a huge array of VPNs available and at an impressive price range making it accessible for every man. Bottom lineLike every other process in the world, cryptocurrency transactions come with their own sets of pros nd cons. But, the distinguishing factor, in this case, is the easy availability of security methods like those of hot and cold wallets, VPNs, and offline private key. Taking a course to any of the above-mentioned methods will guarantee the security of your transaction to a great extent. |
| You are subscribed to email updates from My Blogger Tricks. To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google, 1600 Amphitheatre Parkway, Mountain View, CA 94043, United States | |